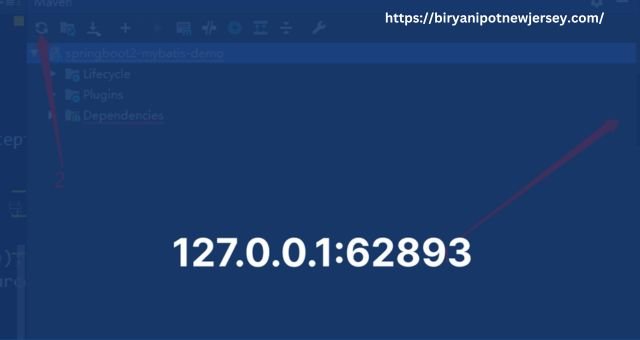
Have you ever encountered the cryptic address 127.0.0.1:62893? While working with development tools or software relatively.
Understanding what this address signifies. Also, its potential uses can be valuable knowledge for developers and tech-savvy users.
In this article let’s dance into the world of 127.0.0.1:62893. Dissect its components and explore its application.
What is 127.0.0.1:62893?
127.0.0.1 is reportedly an IP address known as a loopback IP address or localhost. Moreover, it’s a standard part of Internet Protocol (IP) standards.
Further, the number of following the colon is 62893. Here, it represents a specific port number on your computer.
Together, 127.0.0.1:62893 refers to a service. Or an application running on your computer, accessible through port 62893.
127.0.0.1:62893 – Overview
Here, this numerical combination is a cryptic address. Further, it can be also broken down into two parts.
The LocalHost 127.0.0.1
This IP address is reportedly a look-back Internet Protocol address called “localhost”. Further, it directs back to the network itself.
Moreover, it establishes an IP connection with a system (computer). Here, being a host loop, it should “loop” back to the computer itself.
Further, this means that any data package should not go outside the host. 127.0.0.1 network back to the component computer.
The developer uses 127.0.0.1 to test the applications. It works in a similar way by connecting to any device. However, it doesn’t use LAN.
The Port Address 62893
62893 is reportedly a port number that identifies a specific process. 462893 is not one of the well-known definitions. Especially by the Internet Assigned Numbers Authority (IANA).
This popular port is commonly used for standard service. Such as HTTPS (port 80) and HTTPS (port 443).
However, 62890 falls within the range of short-lived ports (49152-65535). The ports in this range are dynamically allocated reportedly. Especially by the operating system for temporary use.
Benefits of Using 127.0.0.1:62893
Here, this address offers various benefits to the developer.
- Streamlining the Development
- Testing
- Networking to Debugging
- Offering an isolated environment for a safe and fast development process.
Is Exposing Port Publicly Safe?
While port 62893 itself does not inherently force a security risk. However, exposing it publicly without paper precautions can potentially compromise security. Especially in your network and systems.
Here’s why exposing ports publicly can be unsafe respectively.
Security Exploits
462893 uses Memcached which itself might have vulnerabilities. These vulnerabilities can be for unauthorized access to your system. If the port is publicly accessible.
Denial of Service (DoS) Attacks
Memcached is susceptible to DoS attacks. It can here overload your system with requests and crash it. Exposing the port makes your system a target for such attacks.
Unauthorized Access
Anyone with Internet access can potentially try to connect to your Memcached server. If the port is unfortunately public. This also increases the chance of unauthorized access.
127.0.0.1:62893 – Safety Tips and Best Practices
Regularly scan your network for open ports. So, it can identify any unexpected service running on one port or another port.
Implement Access Control List (ACLs) and authentication mechanism. Especially to restrict access to the port. Based on the principle of least privilege relatively.
Configure firewall rules to filter incoming and outgoing traffic on the port. So, it can allow only necessary connection
Ensure that communication is always encrypted using the protocol. Such as TLS (Transport Layer Security). If sensitive data is further transmitted over port 62893.
Moreover, monitor network traffic and log activities related to ports. Since it detects and responds to suspicious behavior promptly.
127.0.0.1:62893 – Troubleshooting Tips
Restart the service or give commands. So, it can run web servers and development tools.
Further, use a different port number. By simply going to the application configuration settings respectively.
Configure the fireball by using terminal commands. Such as Linux iptables. For Windows, visit the control panel. Then, go to “System and Security”.
Here, select “Windows Defender Firewall”. After this in advance, go to the inbound role. Then, rules for the port.
Ensure proper working of application for specific configurations. Then, Leverage Network Diagnostic Tools.
Disadvantages
462893 uses Memcached which itself might have vulnerabilities. These vulnerabilities can be for unauthorized access to your system. If the port is publicly accessible.
Memcached is susceptible to DoS attacks. It can here overload your system with requests and crash it. Exposing the port makes your system a target for such attacks.
Anyone with Internet access can potentially try to connect to your Memcached server. If the port is unfortunately public. This also increases the chance of unauthorized access

Conclusion
127.0.0.1 is reportedly an IP address known as a loopback IP address or localhost. Moreover, it’s a standard part of Internet Protocol (IP) standards.
Further, the number of following the colon is 62893. Here, it represents a specific port number on your computer. Together, 127.0.0.1:62893 refers to a service. Or application running on your
While port 62893 itself does not inherently force a security risk. However, exposing it publicly without paper precautions can potentially compromise security. Especially in your network and systems.
Disclaimer
We hope that all the information provided satisfies your curiosity. However, we can’t guarantee that all the information is 100% accurate.